Tier 0 Information Security
Incident Responder ITs version of the first responder Skills. Show activity on this post.
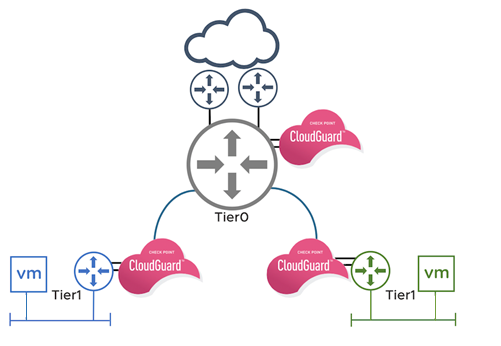
Cloudguard For Nsx T Service Insertion At The Edge Service Chaining
Tier 0 is where the crown jewels are kept.

Tier 0 information security. Specifically forest and domain administration privileges. The naming of these tiers can also vary by company. IT technical support tiers are typically identified by numbers.
Anti-Malware admins for Tier 0 servers. The extra tier is built to provide an environment to meet requirements in Policy 412 Data Stewardship and Custodianship Policy 510 Information Security and also to allow Service Owners to comply with applicable laws and regulations such as HIPAA Health Insurance Portability and Accountability Act FERPA Family Educational Rights and Privacy Act PCI payment card industry. Virtualization admins for Tier 0 servers.
Tier 1 organizations have ineffective risk management methods Tier 2 have informal risk management methods Tier 3 have structured risk management methods and Tier 4 have adaptive risk management methods. Tier 4 is designed to host mission critical servers and computer systems with fully redundant subsystems cooling power network links storage etc and compartmentalized security zones controlled by biometric access controls methods. SOC analysts are organized in four tiers.
Tier 2 Security Analyst. Were glad to help you enjoy absolute freedom privacy and security online. Risk Tier 1 vendors will be classified as business and.
Tier 0 administrator accounts include accounts groups and other assets that have direct or indirect administrative control of the on-premises Active. If you isolate those activities and accounts that have that level of access to Tier 0 you can isolate use of DA privileged accounts to that forest. Emergency Access to the production forest.
Real threats are passed to a Tier 2 analyst with deeper security experience who conducts further. Federal Information Security Management Act Law enacted by Congress - part of the E-Gov Act of 2002 Applies to federal organizations and their contractors Requires implementation of information security protections commensurate with the risk and magnitude of the harm NIST National Institute of Standards and Technology. Privva has a 4-tier vendor classification system based on data access network or physical access and business criticality.
Authorizing Official AO or Designated RepresentativeResponsible for accepting. Level 1 Damage of the information system results in harm to the legal rights of citizens legal persons and other organizations but will not harm national security social order or public interest. Tier 1 organizations have ineffective risk management methods.
Tier 0 Tier 1 Tier 2 and so on. SOC Roles and Responsibilities. Tier 0 scope expansion.
A Data center performance b Investment c ROI return on investment Tier 4 data center considered as most robust and less prone to failures. All of the above natural ability dogged curiosity to get to the root cause and the ability to remain calm under pressure. There is no official tier certification for Microsoft.
Internet Customer Premises BGP BGP VGW IGW BGP Direct Connect Interface VPC Interface Internet Interface. Traditional paper-based keys and keys for Secure Telephone Unit - Third Generation STE FNBDT Iridium Secure Data Network System SDNS and other electronic key are managed from an underground building in Finksburg Maryland which is capable of the following. AD Topology and Replication admins.
Initially SIEM alerts flow to Tier 1 analysts who monitor prioritize and investigate them. Use ZeroTier to create products which run on their own decentralized networks. Uptime which its the institute that manages Tiers certification doesnt have Microsoft listed in their certified Tier Database.
You also avoid generic accounts for audit purposes. Cyber security software fits into architecture that can be divided into well-defined tiers of servers that allows for efficient and flexible upgrading when new technology needs to be added. Roles suitable for managing the tier 0 production forest accounts and resources might include.
Create a 5G-capable secure P2P network for any IoT device that can run on 64MB of RAM. Senior Information Security OfficerResponsible for carrying out the chief information officer security responsibilities and serving as the primary interface between senior managers and information system owners. What does it mean.
The idea is administrator level users never have access to anything but tier-0 to avoid token compromises ect. You have the main administrators in Tier-0 and End users in Tier-2 for example sakes. Tier 1 handles east-west traffic traffic between routed network segments within the SDDC.
Tier 0 - Enterprise production forest. In this TorGuard Vs IPVanish comparison review were going to compare these two VPN services based on factors such as. The MLPS sets five levels of information security based on potential consequences of damaged information systems.
The CF also referred to as Tier 0 is the foundation of EKMS. Thats why there is no official certification. Users also use apps to access service catalogs where they can request and receive services without involving the IT staff.
Watching a video series about Active Directory and doing security based on tiers. Tier 0 expands to become the control plane and addresses all aspects of access control including networking where it is the onlybest access control option such as legacy OT options. Being a former white hat hacker is also a big plus.
General product and services gather information analyze symptoms tier II investigate issues raised from tier 1 support and check for known solutions to complex issues and tier III handles the most difficult problems and are experts in their field often conducts research and. Tier 0 handles north-south traffic traffic leaving or entering the SDDC or between the Management and Compute gateways. Classifying vendors by Tier so you can ask relevant questions during your security review process is a critical step in the vendor risk management program lifecycle.
ZeroTier provides network control and P2P functionality. Different companies organize their tiers of IT support differently according to staff size and expertise. These four Tiers are summarized below.
This tier provides the IT team with instructions on how cyber security procedures implemented in the logical tier have been updated for risk-based management decisions. To increase clarity and actionability what was. My question is this.
With numerous VPN services available there should be a Zero Tier Vpn lot of scrutinies to find the perfect one based on your demands. Users retrieve support information from web and mobile pages or apps including FAQs detailed product and technical information blog posts manuals and search functions. Self-help and user-retrieved information.
Nsx T Lab Logical Routers Gateways Vdives

Auditing Information And Cyber Security Governance A Controls Based A

Security Risk Management An Overview Sciencedirect Topics
Nsx T Lab Tier 0 Gateway Vdives
Asus Corporate Social Responsibility

Human Aspects Of Information Security In Organisations Sciencedirect

Cyber Adversary An Overview Sciencedirect Topics

Cybersecurity Framework An Overview Sciencedirect Topics
Tiered Base Access Defined Goodfellow Air Force Base Article Display

Cybersecurity Framework An Overview Sciencedirect Topics
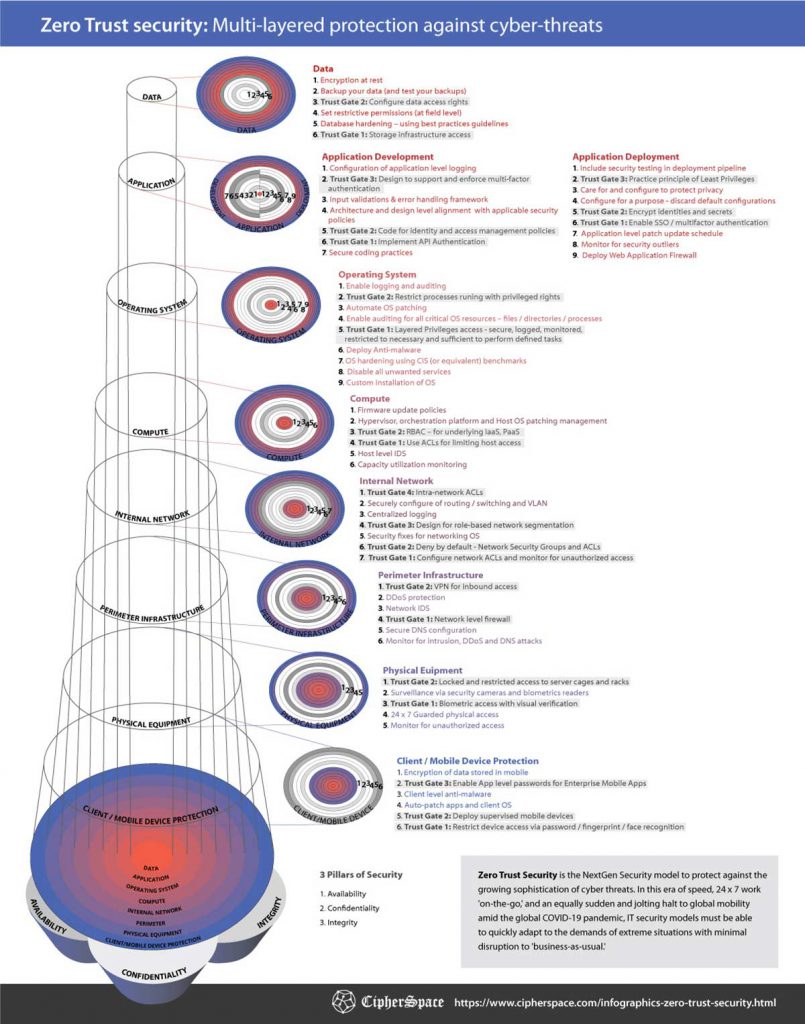
Zero Trust Security Multi Layered Protection Against Cyber Threats Cipherspace
Nsx T Lab Tier 0 Gateway Vdives
Asus Corporate Social Responsibility

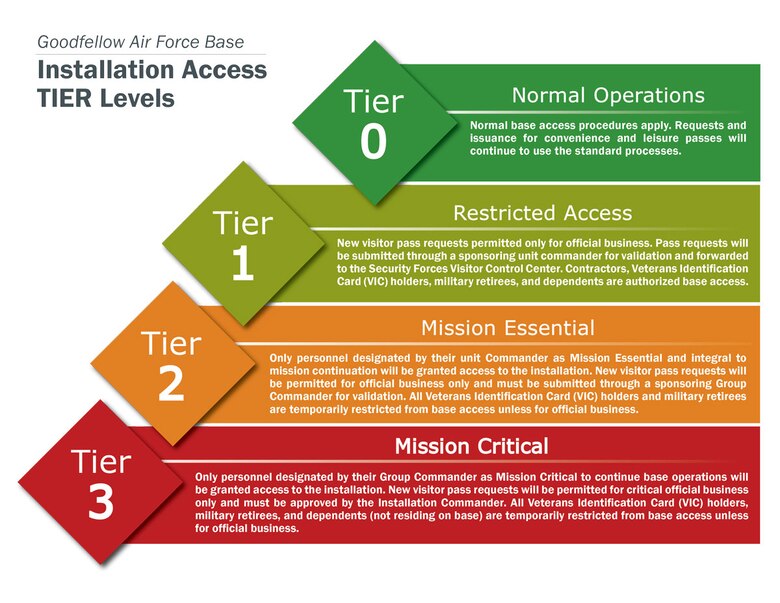

Posting Komentar untuk "Tier 0 Information Security"