N Information Security Which Of The Following Is An Example Of A Threat Actor
The globalized nature of the Internet allows these threat actors to be physically located. In threat intelligence actors are generally categorized as external internal or partner.

Business Launch Invitation Templates Free Vincegray2014 For Business Launch Invitation Templat In 2021 Business Launch Party Business Invitation Corporate Invitation
Insider threats present a complex and dynamic risk affecting the public and private domains of all critical infrastructure sectors.

N information security which of the following is an example of a threat actor. As much as possible a secure system should be simple for those on the inside to understand and use. This problem has been solved. Complex security schemes are often compromised to make them easier for trusted users to work with yet this can also make it easier for the attackers.
This section provides an overview to help frame the discussion of insiders and the threats they pose. A threat actor also called a malicious actor or bad actor is an entity that is partially or wholly responsible for an incident that impacts or has the potential to impact -- an organizations security. Threat intelligence systems are commonly used in combination with other security tools.
Defining these threats is a critical step in understanding and establishing an insider threat mitigation program. Threats to information assets can cause loss of confidentiality integrity or availability of data. It is vital that organizations understand normal employee baseline behaviors and also ensure employees understand how they may be used as a conduit for others to obtain information.
Other groups of Nation State Actors specialise in propaganda and disinformation in cyber space forming armies of trolls that fight back against unfavourable controlled or biased media sources to attempt to raise their employers reputation. A cryptographic key that is used to perform both the cryptographic operation and its inverse for example to encrypt plaintext and decrypt ciphertext or create a message authentication code and to verify the code. Many organizations struggle to detect these threats due to their clandestine nature resource sophistication and their lack of deep understanding of threat actor behavior.
See the answer See the answer See the answer done loading. All of the above. Alternatively as an extension of the states security apparatus the Nation State Actor may be tasked with tracking disrupting and persecuting dissidents or activists.
A person attempting to break into a secure computer network d. Information security policy. In cyber security and threat intelligence a threat actor is a broad term for any individual or group of individuals that attempts to or successfully conducts malicious activities against enterprises whether intentionally or unintentionally.
In information security which of the following is an example of a threat actor. Advanced threat actors such as organized cybercriminals nation-states and corporate spies represent the greatest information security threat to enterprises today. The following product is intended to act as a springboard for organizations to consider.
A virus that attacks a computer network c. A threat actor is a person or entity that has the ability or intent to impact the security of other individuals or companies. In information security which of the following is an example of a threat actor.
The unintentional insider threat. Threat intelligence helps organizations understand potential or current cyber threats. A force of nature such as a tornado that could destroy computer equipment b.
It is a very general concept. Complex security systems can be hard to understand troubleshoot and feel secure about. In cybersecurity it is more common to talk about threats such as viruses trojan horses denial of service attacks.
Phishing emails is a social engineering threat that can cause eg loss of passwords credit card numbers and other sensitive data. With external threat actors no trust or privilege previously exists while with internal or partner actors some. Cyber threat actors are states groups or individuals who with malicious intent aim to take advantage of vulnerabilities low cyber security awareness or technological developments to gain unauthorized access to information systems in order to access or otherwise affect victims data devices systems and networks.
The more information security staff have about threat actors their capabilities infrastructure and motives the better they can defend their organization.

7 Types Of Cyber Threat Actors And Their Damage

Use Case Diagram Tutorial Guide With Examples Creately Blog Use Case Check And Balance Tutorial

Destiny 2 4k Wallpaper Reddit Gallery Wallpaper Iphone Neon Vaporwave Wallpaper Wallpaper

School Threat Assessment Template New Example Of A Location Risk Assessment Sheet Risk Management Safety Management System Risk Analysis
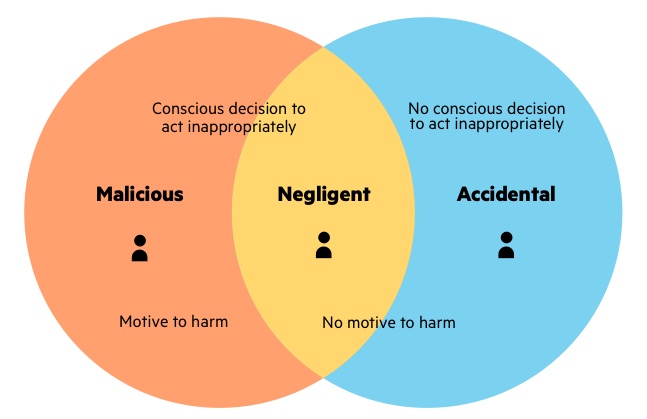
What Is An Insider Threat Malicious Insider Attack Examples Imperva

The 3 Types Of Security Controls Expert Explains Purplesec

Cyber Security Threats And Attacks All You Need To Know

Duskwood Jake Edit Youtube In 2021 Jake Edit Dusk
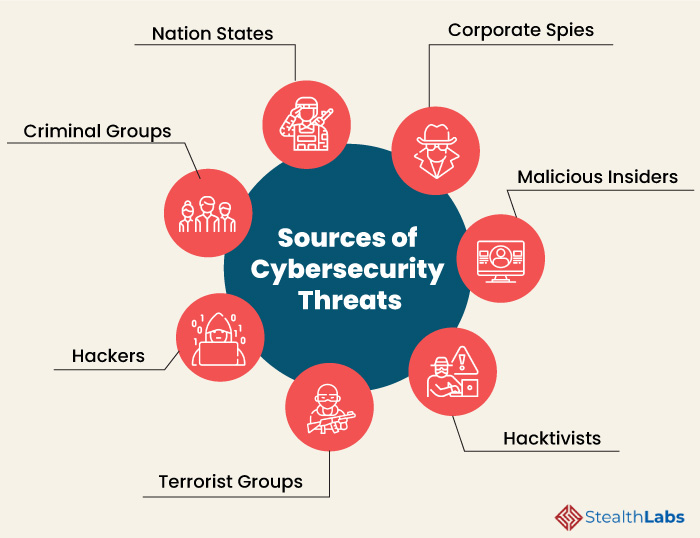
Cyber Security Threats And Attacks All You Need To Know

Election Security Spotlight Cyber Threat Actors
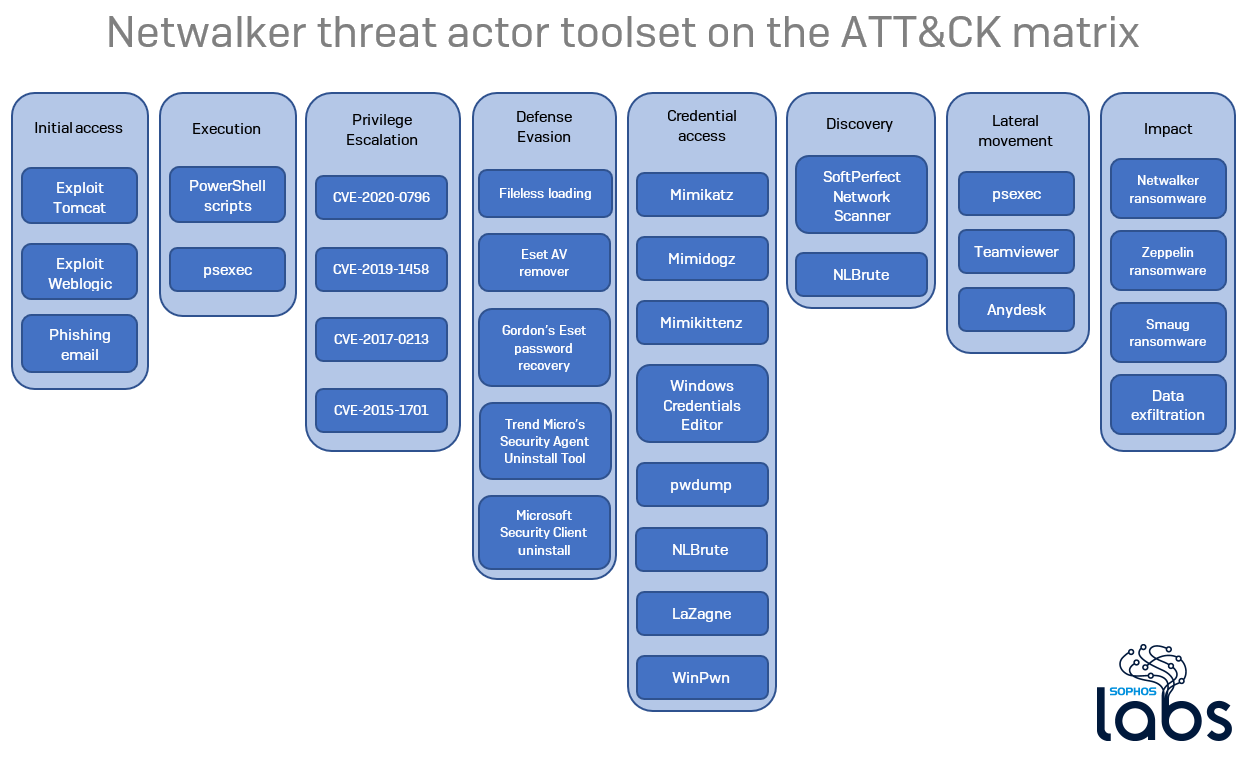
Netwalker Ransomware Tools Give Insight Into Threat Actor Sophos News

Pin By Curso Conserto Celular On Festa Android Application Android Android App Icon Android App Development

Threat Modeling 12 Available Methods

Pin By Dan Williams On Cyber Security Ddos Attack Denial Attack
Posting Komentar untuk "N Information Security Which Of The Following Is An Example Of A Threat Actor"